Online Forums
Technical support is provided through Support Forums below. Anybody can view them; you need to Register/Login to our site (see links in upper right corner) in order to Post questions. You do not have to be a licensed user of our product.
Please read Rules for forum posts before reporting your issue or asking a question. OPC Labs team is actively monitoring the forums, and replies as soon as possible. Various technical information can also be found in our Knowledge Base. For your convenience, we have also assembled a Frequently Asked Questions page.
Do not use the Contact page for technical issues.
- Forum
- Discussions
- QuickOPC-UA in .NET
- Unauthorized Access Exception Browsing Endpoint Application Pool Identity
Unauthorized Access Exception Browsing Endpoint Application Pool Identity
It might work - please print out the above value from inside the Web app to check if it points where you want it to... and if so, you can try place the Certificate Generator there (and disable the prerequisite boxing).
Regards
Please Log in or Create an account to join the conversation.
Please Log in or Create an account to join the conversation.
What wanted to say that just installing the UA Certificate Generator wouldn't help by itself. But it should help together with disabling the prerequisite boxing, as per instructions (kb.opclabs.com/How_to_disable_prerequisites_boxing ). Note that the XML fragment will have to go to the .config file for the process - which might the IIS app pool executable.
If you install one of the OPC Foundation setups that include the UA Certificate Generator, QuickOPC should find it.The search is done inside the SDK (which we cannot easily change and is one of the contributing factors to the necessity of all these workarounds). By briefly looking at that algorithm, it looks like that it searches:
1. "Opc.Ua.CertificateGenerator.exe" in the base directory of the current AppDomain.
2. "Bin\Opc.Ua.CertificateGenerator.exe" under the current directory (of the process).
3. Repeats Step 2 for parent directories until the root is reached.
4. "OPC Foundation\UA\v1.0\Bin\Opc.Ua.CertificateGenerator.exe" under CommonProgramFiles.
5. As Step 4 but with " (x86)" added to the CommonProgramFiles directory.
Best regards
Please Log in or Create an account to join the conversation.
Please Log in or Create an account to join the conversation.
[Edited later: Actually it is not the Certificate Generator that is placed into the physical temp directory; it needs to be in a specific location. What gets placed there are parts of the "boxing" library.]
Under environments with tightly controlled security (like IIS), finding the right directory may fail. What QuickOPC should do, in case it finds that the temp directory exists but cannot be accessed, is to silently proceed to the next directory in the list. There appears to be a bug currently, and that's why you have received the exception. I have made a note and we will fix the bug in the next version. But even if the bug wasn't there, other temp directories are likely to be inaccessible as well, so the boxing attempt will probably fail anyway.
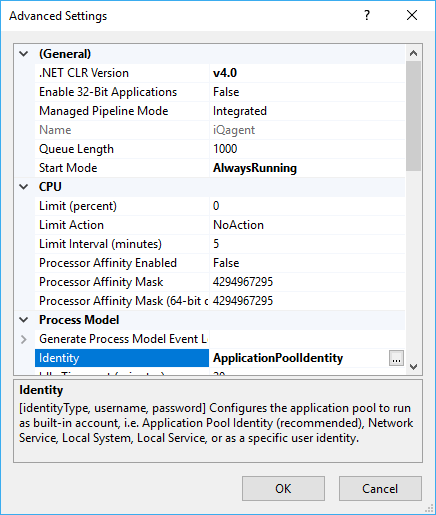
To sum it up, using IIS with OPC UA stack is a challenge. One possible solution is to install the UA Certificate Generator manually (but given the presence of the bug, this won't probably help right now). Other solution is to give the necessary IIS identity access to the temp directory/directories. The first one that QuickOPC currently tries to use is the current user's temporary folder, as returned by the Path.GetTempPath method: docs.microsoft.com/en-us/dotnet/api/system.io.path.gettemppa...d%3Dtrue&view=netframework-4.8 . I believe that "current user" in the IIS context means the identity you selected under the "Process Model" category.
Best regards
Please Log in or Create an account to join the conversation.
Please Log in or Create an account to join the conversation.
This appears to be related to prerequisite boxing - see opclabs.doc-that.com/files/onlinedocs/QuickOpc/Latest/User%2...ml#Prerequisites%20Boxing.html .
You can try to:
1. Give the application pool identity access to the path indicated in the exception
System.UnauthorizedAccessException: Access to the path 'C:\Windows\TEMP\bxsdk32.dll' is denied.
2. Disable prerequisites boxing: kb.opclabs.com/How_to_disable_prerequisites_boxing
Best regards
Please Log in or Create an account to join the conversation.
This is what my settings look like in iis
Is it possible that Application Pool Identity is causing this issue, or could it be something else? If so, what could it be?
Please Log in or Create an account to join the conversation.
- Forum
- Discussions
- QuickOPC-UA in .NET
- Unauthorized Access Exception Browsing Endpoint Application Pool Identity